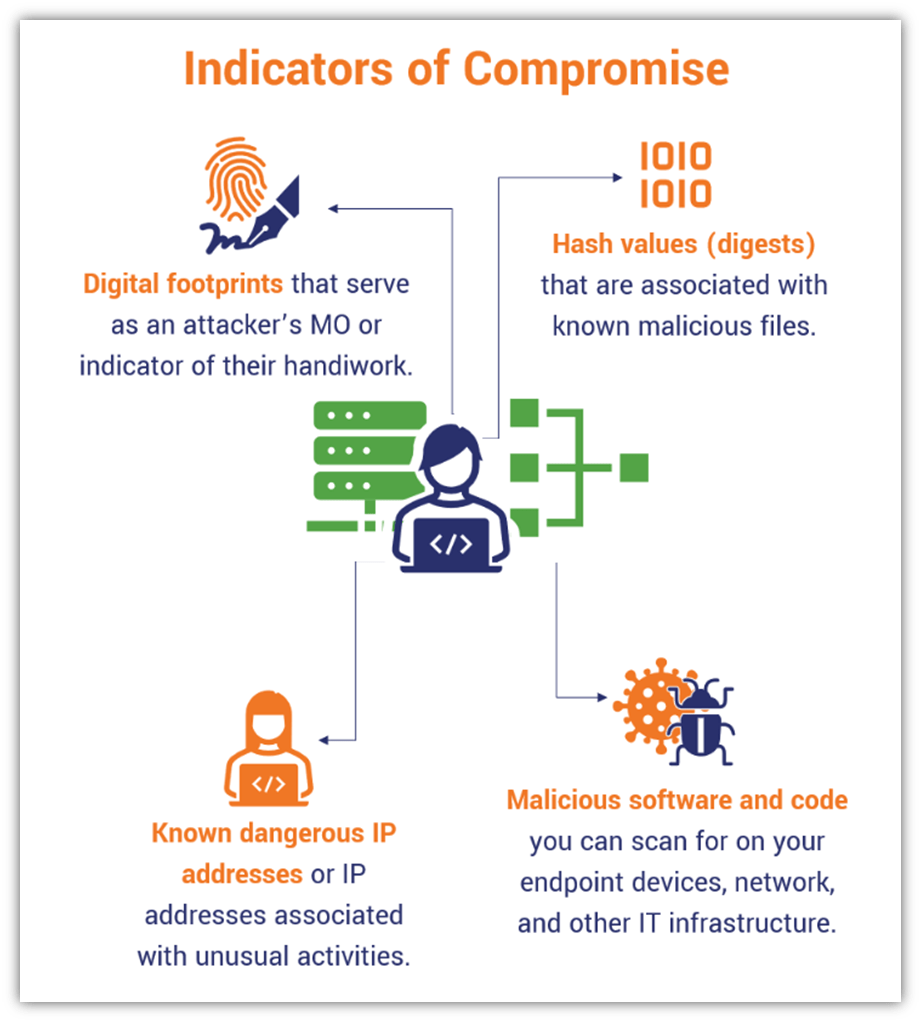
Lapsus$ Indicators Of Compromise . lapsus$ operated against the backdrop of a dynamic ecosystem of threat actors, each having specific tactics, preferring certain. indicators of compromise (iocs) nvidia was targeted by lapsus$ group last month. indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in understanding and mitigating this threat. lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures.
from www.xcitium.com
indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. lapsus$ operated against the backdrop of a dynamic ecosystem of threat actors, each having specific tactics, preferring certain. indicators of compromise (iocs) nvidia was targeted by lapsus$ group last month. in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures. lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in understanding and mitigating this threat.
What are Indicators of Compromise Security? IOC Meaning
Lapsus$ Indicators Of Compromise in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures. lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. indicators of compromise (iocs) nvidia was targeted by lapsus$ group last month. in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures. indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in understanding and mitigating this threat. lapsus$ operated against the backdrop of a dynamic ecosystem of threat actors, each having specific tactics, preferring certain.
From telefonicatech.com
Indicators of Compromise, Key to Detecting and Solving Incidents in an Lapsus$ Indicators Of Compromise although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in understanding and mitigating this threat. lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well. Lapsus$ Indicators Of Compromise.
From www.upguard.com
What are Indicators of Compromise (IOCs)? UpGuard Lapsus$ Indicators Of Compromise although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in understanding and mitigating this threat. indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation. Lapsus$ Indicators Of Compromise.
From blogs.cisco.com
Indicators of Compromise and where to find them Cisco Blogs Lapsus$ Indicators Of Compromise lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in understanding and. Lapsus$ Indicators Of Compromise.
From www.youtube.com
How to Generate an Indicator of Compromise (IOC) File YouTube Lapsus$ Indicators Of Compromise lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in understanding and. Lapsus$ Indicators Of Compromise.
From www.trendmicro.com.ph
Indicators of compromise Definition Lapsus$ Indicators Of Compromise indicators of compromise (iocs) nvidia was targeted by lapsus$ group last month. although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in understanding and mitigating this threat. lapsus$ operated. Lapsus$ Indicators Of Compromise.
From www.makeuseof.com
What Do the Indicators of Compromise Mean? The Best Tools to Help Lapsus$ Indicators Of Compromise indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. indicators of compromise (iocs) nvidia was targeted by lapsus$ group last month. lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. lapsus$ operated against the backdrop of a. Lapsus$ Indicators Of Compromise.
From cyberhoot.com
Indicators of Compromise (IoC) CyberHoot Lapsus$ Indicators Of Compromise indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. indicators of compromise (iocs) nvidia was targeted by lapsus$ group last month. in this threat briefing, we report on. Lapsus$ Indicators Of Compromise.
From www.youtube.com
Understanding Indicators of Compromise for Incident Response YouTube Lapsus$ Indicators Of Compromise lapsus$ operated against the backdrop of a dynamic ecosystem of threat actors, each having specific tactics, preferring certain. lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures. . Lapsus$ Indicators Of Compromise.
From www.youtube.com
What are the Indicators of compromise YouTube Lapsus$ Indicators Of Compromise indicators of compromise (iocs) nvidia was targeted by lapsus$ group last month. in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures. lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. indicators of compromise (iocs) and ttps. Lapsus$ Indicators Of Compromise.
From hackforlab.com
Indicator of Attack vs Indicator of Compromises Lapsus$ Indicators Of Compromise lapsus$ operated against the backdrop of a dynamic ecosystem of threat actors, each having specific tactics, preferring certain. indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures.. Lapsus$ Indicators Of Compromise.
From www.lepide.com
What are Indicators of Compromise? Lapsus$ Indicators Of Compromise indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. indicators of compromise (iocs) nvidia was targeted by lapsus$ group last month. lapsus$ operated against the backdrop of a dynamic ecosystem of threat actors, each having specific tactics, preferring certain. in this threat briefing, we report on. Lapsus$ Indicators Of Compromise.
From www.linkedin.com
The Importance and Difference Between Indicators of Attack and Lapsus$ Indicators Of Compromise although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in understanding and mitigating this threat. indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation. Lapsus$ Indicators Of Compromise.
From blogs.cisco.com
Indicators of Compromise and where to find them Cisco Blogs Lapsus$ Indicators Of Compromise in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures. indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are. Lapsus$ Indicators Of Compromise.
From publish.obsidian.md
indicators of compromise Cyber MiSC Obsidian Publish Lapsus$ Indicators Of Compromise in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures. indicators of compromise (iocs) nvidia was targeted by lapsus$ group last month. indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. although there are no public. Lapsus$ Indicators Of Compromise.
From www.xcitium.com
What are Indicators of Compromise Security? IOC Meaning Lapsus$ Indicators Of Compromise indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures. lapsus$ operated against the backdrop of a dynamic ecosystem of threat actors, each having specific tactics, preferring certain.. Lapsus$ Indicators Of Compromise.
From www.sekoia.io
What is an Indicator of Compromise (IoC)? SEKOIA.IO Lapsus$ Indicators Of Compromise indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. lapsus$’s action on objectives appears to focus on data exfiltration of sensitive information as well as destruction or. although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to. Lapsus$ Indicators Of Compromise.
From www.wallarm.com
What are Indicators of Compromise (IOC)? Lapsus$ Indicators Of Compromise lapsus$ operated against the backdrop of a dynamic ecosystem of threat actors, each having specific tactics, preferring certain. indicators of compromise (iocs) and ttps are admittedly still limited, but lapsus$ developed a reputation for notoriety, using what. in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures.. Lapsus$ Indicators Of Compromise.
From arcticwolf.com
Understanding Indicators of Compromise I Arctic Wolf Lapsus$ Indicators Of Compromise in this threat briefing, we report on the victims of lapsus$ (section 2), the group’s main tactics, techniques and procedures. although there are no public indicators of compromise (iocs), and no tactics, techniques and procedures (ttps) that are unique to lapsus$ group, here we will summarize what is known of this threat actor to better enable defenders in. Lapsus$ Indicators Of Compromise.